Analyzing The GRU's Disruptive Playbook: Tactics and Impact
Since russia invaded Ukraine in February 2022, the world has witnessed a significant escalation in cyber operations by russia's military intelligence agency, known as the GRU. Mandiant, the leading cybersecurity firm, has closely monitored and analyzed the GRU's tactics, and as a result, unveiled a standard five-phase playbook that underpins their subversive operations. This article examines key components of the GRU's playbook, its integration into the ongoing war in Ukraine, and its potential implications for future crises and conflicts involving large-scale subversive cyber operations.
Integration into Ukraine's War
The GRU actively conducts cyber operations to support a broader conflict between russia and Ukraine, which are integrated into the overall war strategy, complementing traditional military actions.
Using reports such as M-Trends 2023 and other resources available in Ukraine Crisis Resource Center, Mandiant has carefully tracked and categorized these cyber operations into six phases. These phases encompass various aspects, such as gaining access to target systems, conducting cyber espionage, executing disruptive attacks, and engaging in information operations.
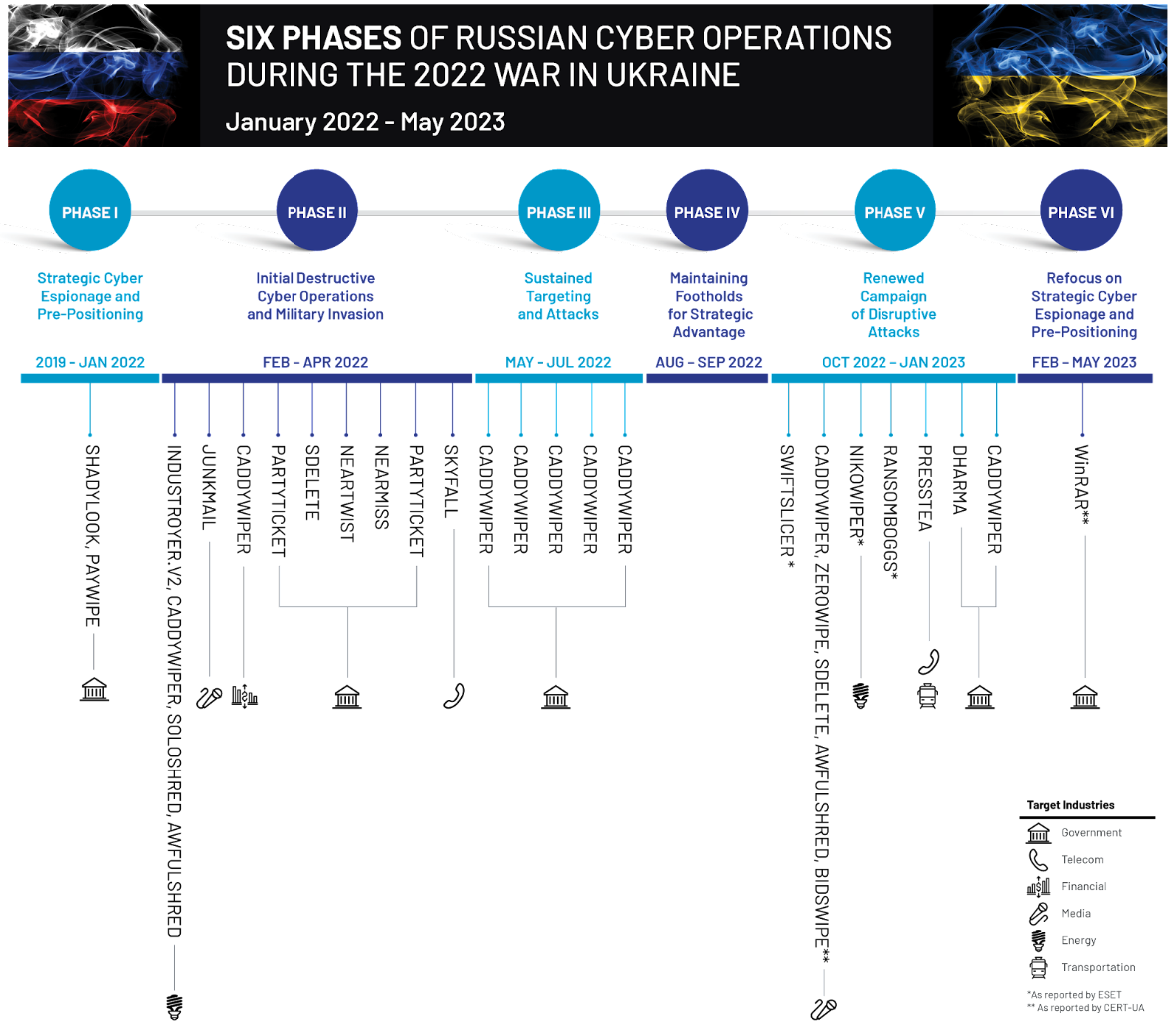
The GRU's 5-Phase Playbook. Tactics Overview
Although much attention is paid to the use of windshield wipers and the perceived success of sabotage operations, it is important to recognize that the GRU uses a comprehensive approach that includes five key components that combine cyber and information operations to create a unified and effective military capability.
- Living on the Edge: The GRU leverages compromised edge infrastructure, such as routers, VPNs, firewalls, and mail servers, to gain and maintain initial access to target networks.
- Living off the Land: The GRU employs built-in tools (operating system components) or pre-installed software in the victim's environment for reconnaissance, lateral movement, and information theft, likely aiming to limit their malware footprint and evade detection.
- Going for the GPO: The GRU creates persistent, privileged access using Group Policy Objects (GPOs) to deploy disruptive payloads, such as "pure" wipers and ransomware.
- Disrupt and Deny: Utilizing "pure" wipers and other low-equity disruptive tools, including ransomware, to suit diverse contexts and scenarios.
- Telegraphing "Success": By employing hacktivist personas on Telegram, the GRU amplifies the narrative of successful disruption, regardless of the actual impact of the operation.
UNC3810. Infiltration Tactics
UNC3810, one of the key threat groups, actively employs this playbook in practice. The primary goal of UNC3810: espionage and disruptive operations against Ukrainian organizations since the onset of russia's actual invasion, as well as credential theft operations against a wide range of global public and private industrial organizations.
- Living on the Edge: In July 2022, UNC3810 gained initial access to the target environment, likely through a VPN compromise. Afterward, they accessed multiple Linux servers and deployed webshell backdoors to establish redundant access points and further penetrate the victim's network.
- Living off the Land: UNC3810 utilized a tactic of leveraging existing tools in the victim's environment to penetrate target networks, including PowerShell, wmiexec, PortProxy, Impacket, and Chisel. After gaining access and establishing a foothold on Linux servers through an unknown webshell, the group deployed a specialized Go-based TCP tunneling tool named GOGETTER. They concealed the tool's presence by aligning its binary modification dates with legitimate files and executed it as a systemd service. The actors also attempted to manipulate packet filtering rules, evident from the misspelled command "iptables-restor," enabling an extended period of unauthorized network access and lateral movement for approximately three months.
- Going for the GPO: UNC3810 effectively establishes persistence, escalates privileges, and deploys wipers using TANKTRAP (on Github called PowerGPOAbuse), a script designed to deploy payloads through Group Policy Objects (GPOs). After successfully adding or modifying GPOs, the actor can download additional files, create services, and schedule tasks that execute across all systems linked to the Active Directory domain. In the UNC3810’s October intrusion, UNC3810 deployed the CADDYWIPER payload within the target network through modified GPOs. To achieve this, after execution, TANKTRAP generated two files: Files.xml (for retrieving CADDYWIPER from the C2 server) and Scheduledtasks.xml (for execution).
- Disrupt and Deny: GRU operations often conclude with deploying wipers or disruptive tools for immediate impact and erasing attacker traces. The most frequently used CADDYWIPER is a wiper known for overwriting files and partitions with null bytes, evolving over time to evade detection. On October 3, 2022, the first CADDYWIPER sample was launched. In one instance, the CADDYWIPER x64 variant was initially blocked by antivirus. UNC3810 then recompiled it as a x32 variant, likely achieving successful execution. Another CADDYWIPER x32 variant, compiled later, had minimal impact due to incompatible group policy settings and system readiness, hindering UNC3810's disruption attempts.
- Telegraphing "Success": To amplify the impact of their attack, UNC3810 employed a hacktivist persona called "CyberArmyofRussia_Reborn" on Telegram to claim responsibility for the wiper attack.
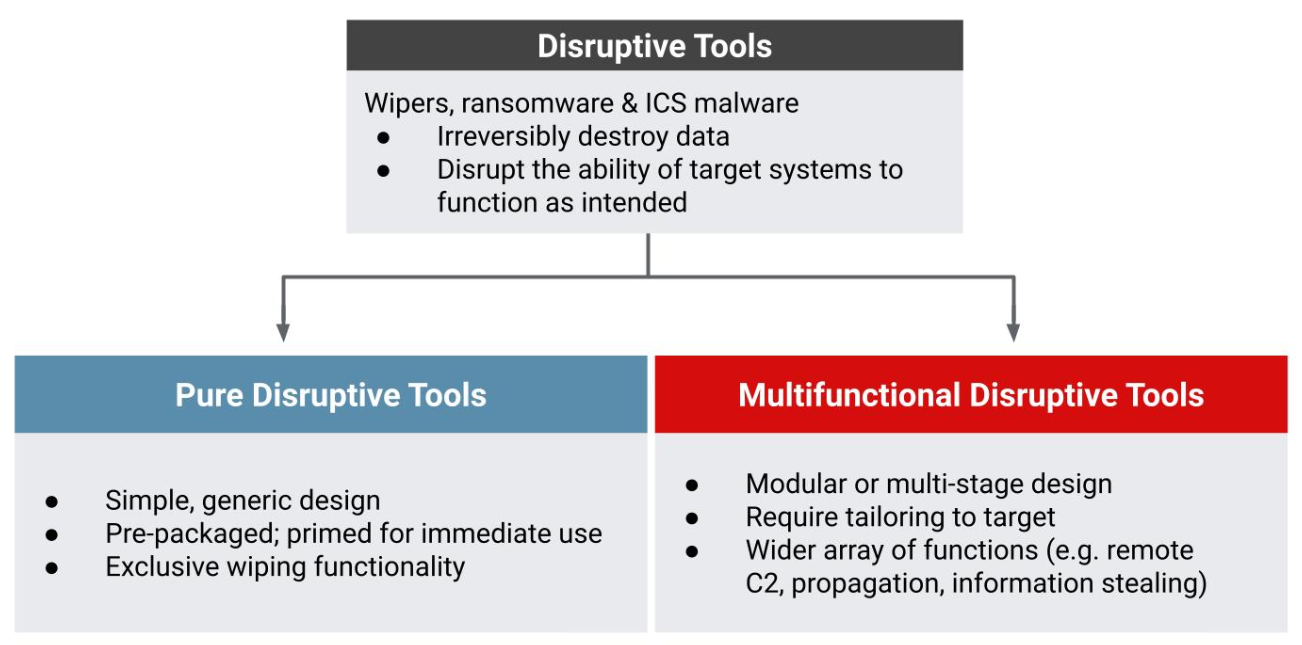
Shift to “Pure” Disruptive Tools
russia's GRU has transitioned to using "pure" disruptive tools, a shift from their historically multifunctional and more complex disruptive tools. These "pure" tools are designed for immediate use, containing only necessary capabilities for disrupting systems. Their lightweight design allows for rapid integration and deployment, maintaining minimal presence until usage.
Obfuscation of identity and psychological manipulation
The GRU purposefully, and sometimes accidentally, assigns its activities to known political actors or groups for difficulties in identification and creation of psychological manipulations. CyberBerkut, CyberCaliphate, Yemeni Cyber Army, Guccifer 2.0, AnPoland, Fancy Bears' Hack Team - GRU copies the tactics, techniques and procedures of these hacktivists.
Amplifying GRU Influence By Hacktivist Collaborations
During the full-scale invasion, russia expanded its capabilities by involving hacktivist groups in its activities. Using these groups, they seek additional support and enhance their influence by exaggerating their achievements. The use of the Telegram social network enables the dissemination of this information and the recruitment of volunteer cyber groups. Various hacktivist groups, such as CyberArmyofRussia_Reborn, XakNet Team, Infoccentr, and Free Civilian, have been and continue to be involved in distributing information about conducted attacks, conducting DDoS attacks, leaking data, and propagating propaganda.
Implications and Future Scenarios
The GRU's operations in Ukraine have showcased russia's strategic adaptations in achieving information confrontation goals, combining cyber and information warfare tactics into a unified playbook. These tactics, while not entirely new, have been innovatively tailored for efficient use in high-stakes, fast-paced wartime scenarios. This purpose-built playbook is likely to influence future conflict situations with similar demands for disruptive cyber operations. Interestingly, parallels can be drawn between these tactics and those employed by financially-motivated ransomware groups, emphasizing a shared aim to expedite initial access to malware delivery and maximize disruptive impact. Consequently, strategies to counter russia's wartime cyber playbook could yield valuable defenses against other ransomware tradecraft as well.





Comments
No comments yet. Be the first to comment!
Leave a Reply
Your email address will not be published.